Engineers and economists team to make communications superhighways viable
The needed spectrum to carry additional communications traffic exists, but government-regulated allocations has some of this space off-limits to wireless providers.
An answer is to share the use of the communications spectrum superhighways in the sky that already exist.
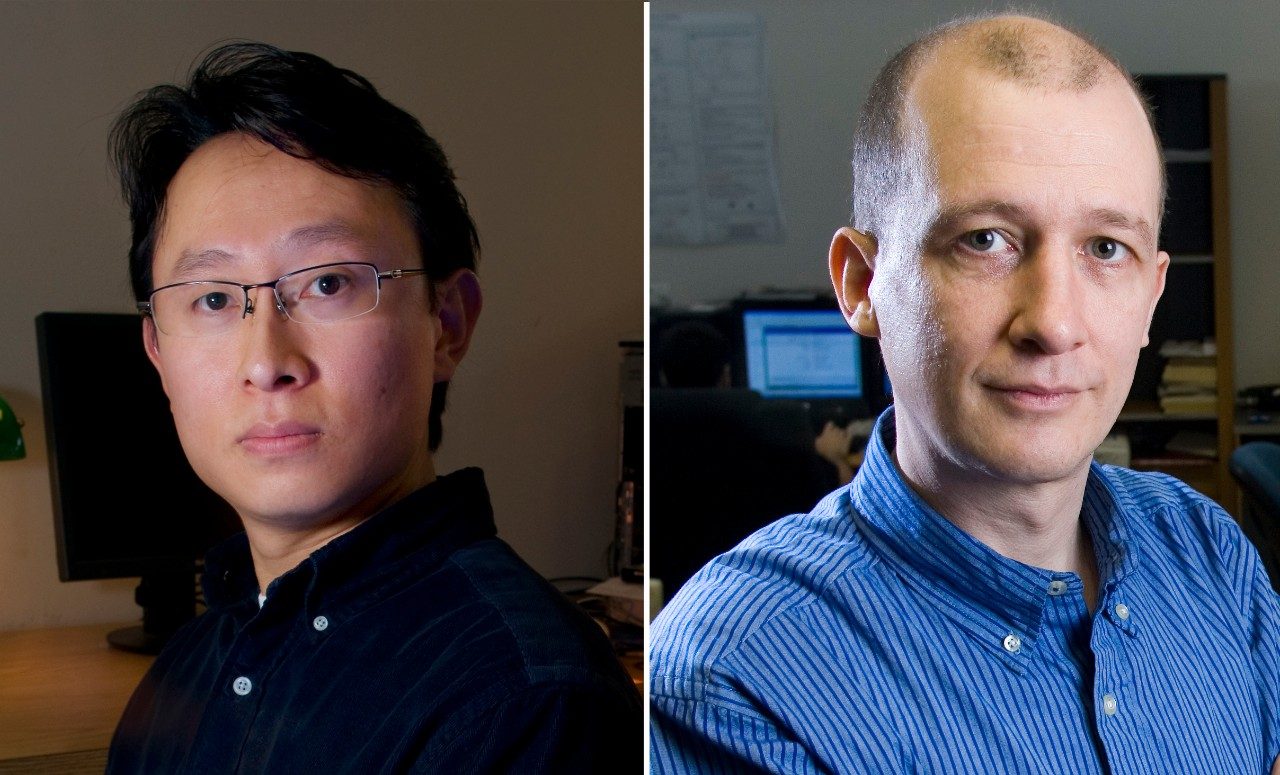
"However, one of the critical challenges that needs to be addressed for spectrum sharing is the problem of spectrum security and enforcement," said Jung-Min "Jerry" Park, Virginia Tech associate professor of electrical and computer engineering. "The primary concern is the interference experienced by primary users due to rogue transmissions by maliciously intended secondary users when the two groups operate in the same band."
To counter this problem, Park and his colleague Patrick Schaumont, also an associate professor of electrical and computer engineering, Michelle Connolly, professor of practice in economics at Duke University, and Nelson Sa, assistant professor of economics at Vassar College, are the principal investigators on a new $1.2 million award from the National Science Foundation's Secure and Trustworthy Cyberspace program.
Virginia Tech holds the largest portion of this interdisciplinary funding, receiving approximately $898,000 of the overall budget.
Their goal is to make trustworthy spectrum sharing technically and economically viable.
The primary users of these crowded, yet invisible superhighways are the license holders or in the case of federal government users, incumbents of a given spectrum. Park politely considers the secondary users "opportunistic".
However, the threat from the opportunists is serious for two reasons, he explained. First, interference caused by rogue transmitters will undermine the advantages of spectrum sharing and seriously hinder its world-wide adoption. Second, cognitive radios that make spectrum sharing possible can be used to launch very destructive jamming attacks.
"Counter measures against these threats can be classified into two enforcement approaches: ex-ante or preventive and ex-post or punitive enforcement. Our research is focused on studying the key mechanisms in both of these enforcement approaches," Park said.
Among his many research projects, Park has previously worked on a privacy enhancing technology to protect children's online privacy, problems of spectrum etiquette in cognitive radio networks, and secure spectrum sensing techniques.
Schaumont is a recipient of an NSF CAREER award to work on hardware and software co-design for secure embedded systems. He has addressed the design of tamper-resistant and efficient cryptography in embedded systems, and constructed a database to support research in secure circuit identifiers.
Tackling the economic considerations of spectrum security and enforcement will be Connolly and Sa. Connolly is a former two-term chief economist for the Federal Communications Commission. Sa is an economic theorist who specializes in industrial organization and economic growth.
The grant will be extended over a four-year period.